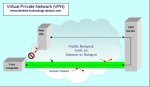
Wireless Internet Protocol
Made the Internet Possible and Making it Better
A new breed of wireless Internet Protocol will
help tame the Internet jungle… where Internet connections were not
guaranteed, were often delayed, and could sometimes even vanish without
trace.
The latest Internet Protocol version 6 (IPV6) will make the Internet faster, more reliable, more secure, allow it to grow and enable ‘always on connections’.But lets go back a few steps...
What is wireless Internet Protocol?
Wireless Internet Protocol is often just called IP. And it isn’t just restricted to wireless – it also applies to other data communications media such as wire or fibre optic cable.
You don’t notice it. Wireless Internet Protocol works in the background. It’s the protocol that makes inter-networking possible – a common language, a set of rules that allows computers, and other electronic devices that use them, to communicate with each other, directly, or across different networks.
So each end of the communications link knows what to expect from the other... they will both follow the same rules.
Wireless Internet Protocol is similar to the protocols we apply in our daily lives, at a social level, to make our interaction with others go more smoothly. We use names. We have expectations of others and accept the expectations that others have of us. We also have traffic rules; protocols that allow cars to share the roads, maximize traffic flow, reduce the likelihood of collisions and help us get to our destinations on time.
We also apply a protocol to Internet traffic to help ensure that the data we send has the best chance of getting to its destination as efficiently as possible.
Each device uses an IP address.
All Internet traffic travels as addressed data packets over media such as wireless, wires or fibre optic cable… but more about that later.
Recent developments in wireless Internet Protocol will be making our Internet experience much better.
Have you ever wondered how Internet traffic travels over the information superhighway, avoiding collisions with other data traffic and bypassing or negotiating obstructions such as equipment breakdowns or traffic jams, minimizing delays by finding the most efficient route on its way to its destination?
The process is made possible by ensuring that Internet-capable devices know where they’re going and what to expect from each other… ensuring they follow standard rules, like road rules; an Internet communications protocol.
Any device that has been designed and manufactured to comply with the IP should be able to work with others that also comply. It’s these IP-compliant devices that make the Internet –and IP makes Internetworking possible.
The wireless Internet Protocol has been carefully designed and structured in layers.
What is Internet Protocol layering?
To ensure that data/information transfer is carried out in an ordered way, the process is divided into a vertical stack of layers, each with its own purpose.
The most evolved system (OSI) for enabling electronic devices to connect to each other has seven layers.
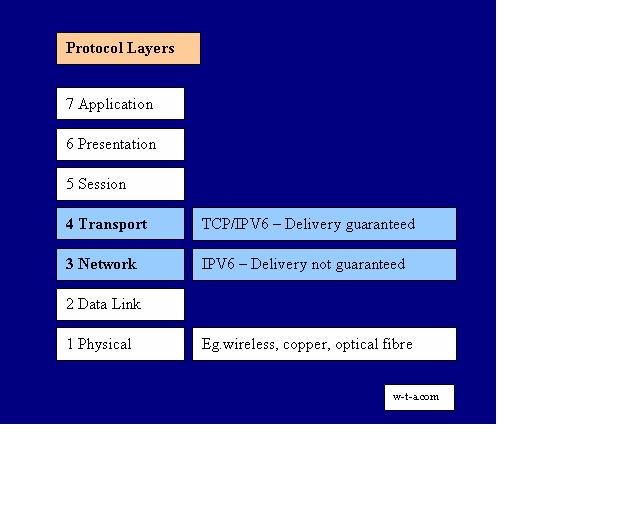
The first and most fundamental layer, 1, is at the bottom. This gives rules for physical media, like wireless, wires, connectors and signal voltages.
The highest level, layer 7, is at the top. This gives the rules that relate most closely to the user experience, such as those used by Internet browsers, like Internet Explorer or Firefox.
Any layer can use the services provided at the layer beneath it – they don’t need to duplicate something that’s already being done at another layer. Each layer has a specific and independent role. If changes are made to one layer it shouldn’t affect the others.
The Internet Protocols are in layer 3, the networking layer and layer 4, the transport layer. These have the rules that allow data to be transferred between different devices, and devices on different networks.
Here’s a simple way to think of layers. Please don’t interpret this too literally; it’s just to give you a feeling for how it works; an informal Internet Protocol definition.
Say we wanted to apply protocol layers to written documents. Then…
Layer 1 may have the rules that show how to form individual letters: a, b, c, d etc. Layer 2 can request and use these.
Layer 2 may have the rules that show how to build words and sentences from letters made using the rules at layer 1.
Layer 3, the layer which includes Internet Protocol, may have the rules that show how to build pages from sentences using services from layer 2. The pages may be numbered, and on each page it would say what book and chapter the page belonged to. In this analogy, pages built from layer 3 rules may be passed up to layer 4.
Layer 4 may contain the rules for making the pages into a book, define how it may be distributed through different libraries and accounted for.
Layers 5, 6 and 7 provide the rules for carrying out successively higher level transfers.
Think of it as a progression of rules, starting at the bottom, with simple data and physical compatibility at layer 1, through to rules for more sophisticated information and processes at the top - layer 7, the applications layer – where complex literature queries may be processed.
But what makes all these rules happen?
Software-computer programs. They perform the service, based on the rules at one layer, and present the results to the level above when requested. The electronic communications device needs a ’software stack’ to enable it to communicate at a higher level, e.g. to inter-network.
So, does IP care what medium the information is sent over? No! Because IP operates at a higher level and has the necessary software programs to ‘delegate’ the ‘wireless, wired or optical tasks’ defined at layer 1.
So electronic devices may typically need to contain a software stack made from elements of layers 1, 2, 3 and sometimes 4 to enable them to inter-network.
What is Internet Protocol Version 4?
In the world of wireless Internet Protocol one version, IPV4, has been the mainstay and is still used. Unfortunately it ran out of permanent address space and has no new addresses to allocate. Was this the result of lack of planning? Probably not, as at the time, no-one could know how big the Internet would become.
To alleviate this pressure on permanent addresses, networks had to find a way around this, so they introduced temporary addresses – ones that weren’t needed all of the time – so were available some of the time - addresses that could be ‘borrowed’ for temporary Internet transactions, then recycled.
But to do this, networks needed to be able to ’translate’ one address into another, a process called Network Address Translation (NAT). This added complexity and delays, as it took time to do a translation… and increased the risk of something going wrong. It was getting messy.
IPV4 needed a successor… and so IPV6 was conceived. Its parents were members of the Internet Engineering Task Force (IETF) and IPV6 was very carefully planned.
The IETF is made up from chapters from different regions around the world, comprising engineers, manufacturers, sellers, users and other interested contributors. It’s only by getting support, co-operation and input from such a wide range of parties that a wireless Internet Protocol, that would suit everyone’s needs, could be created.
What is Internet Protocol Version 6?
After a long gestation, IPV6 was born and started bringing its significant influence to the global village. Over its lifetime IPV6 will increasingly bring major benefits such as…
- speed
- reliability
- security
- expandability…
IPV6 will allow a practically unlimited number of IP devices to each have its own unique address, enabling dedicated, always-on, end-to-end connections.
It will perhaps lead to the so-called ‘Internet of everything’.
These changes won’t of course affect the quality of the content you find on the web or on the effectiveness of search engine searches you make. These have little to do with wireless Internet Protocol.
So just how many addresses can IPV6 make available?
IPV4 has allocated approximately four billion.
That’s 4,000,000,000 addresses.
The estimated world population is in the order of 10 billion.
That’s 10,000,000,000.
IPV4 couldn’t even provide one address for each person.
However, IPV6 can allocate more than 100,000,000,000,000,000,000,000,000,000,000,000,000.
More than enough!!
With IPV6, data packets routed across networks will no longer have to be given temporary addresses. They will keep the same permanent address.
IPV4 address conversions took time and increased the risk of packets getting lost in transit, communication retries and dropped connections. How often have you lost your IPV4 connection while browsing, or not been able to get the connection in the first place?
With IP level 3 there are no guarantees given, or responsibility taken for successful Internet transactions. This is a level 4 function.
Wireless Internet Protocol, TCP/IPV6 at level 4 will improve Internet service and can replace ‘best effort’ with ‘quality and accountability’ for data packet-based message delivery.
So what is a data packet?
Data Packets
A typical wireless Internet Protocol IPV6 packet would contain...
- a header; with all the data needed to get the...
- payload; the actual useful data we want to send or receive...
to its destination, reliably and securely.
The header doesn’t contain useful information, it’s just an overhead, like the wrapper on a conventional packet sent through the physical post. It’s just a thing you need to get it there.
A conventional wrapper creates a safe vehicle for the thing inside, made to suit the medium that it’s sent over (car, plane, boat) complying with the ‘conventional postal service protocol’… it’s within the correct size range, has a stamp, it has a destination address and a return address… like IPV4, there were no guarantees of perfect service with this service either. And when you received it, you’d usually discard the wrapper and keep the thing inside it (the ‘payload’).
The ordinary mail service is like the ‘send and hope’ connectionless communication. There’s no guarantee that a packet will get to its destination. And no one will tell you if it hasn’t... but has other benefits; the overheads and cost are low.
On the other hand, layer 4 TCP/IPV6 enables accountable end-to-end delivery, much like sending a conventional packet by courier – the sender and receiver connect first, then the packet is sent and tracked. If it doesn’t arrive at its destination, the packet will be traced and, if necessary, resent. This is a better quality but higher overhead, higher cost operation.
Because the IPV6 header data also has to be sent, it’s more useful to think of the throughput of useful information (we’re really only interested in receiving the payload), rather than data rate. Throughput tells us about the efficiency of the useful data transaction. The less overhead, compared with useful data, the more efficient the transaction.
Can different protocols coexist on the same network? Yes. Because a wireless internet protocol field in the headers contains the service the packet requires, and as the service is performed, this is removed. If there’s a ’next level up’ service required (say TCP/IPV6), the next header will have ‘TCP’ in its header to indicate that this service is required.
But does IPV6 make inter-networking more secure?
Security
IPsec Internet Protocol Security can help defend against theft, corruption of data and credentials… and hacker attack on networks.
IPsec provides protection at network level (layer 3).
This is important because it can be implemented between networks at packet level rather than having to be set up within a computer application which would require each computer to be specially configured. Because IPsec can be implemented at layer 3 this security service is also available to any of the layers above layer 3.
With IPsec Internet Protocol security data packets may be filtered to restrict who can communicate on the network and provide security for specific IP-enabled networking devices communicating with each other, providing end-to-end security.
However, while IPsec provides high quality security, you should keep the big security picture in mind as IPsec isn’t a complete solution. IPsec provide s the traffic police along the information highway, between two communicating wireless Internet Protocol enabled devices. It also provides a guard at each entrance.
While not usually needing to be high security, even our voice traffic is often being stuffed into data packets and sent over the Internet.
Voice over Internet Protocol - VoIP
To talk over the Internet it’s necessary to change a voice signal into a form that makes it suitable for sending over the Internet. Then the phone has to reconstitute the original sound at the receiving end.
We call sending voice messages over the Internet ‘Voice over Internet Protocol’ or VoIP. The sound signal first needs to be prepared in a special way to make it IP-compatible.
Starting at level 1 we convert the continuous analogue voice signal into a digital signal by rapidly sampling it and producing a series of numbers (digits, i.e. made digital) that represents the original voice.
This digitized voice is broken up into pieces, put into data packets, wrapped with a source and destination address and usually given a special packet number, like a page number, that says what order the packets are being put in.
Think of it like this. If we were to send a document on this way…
Say it has 100 numbered pages and you give a single page to each of 100 people. You tell each person where to deliver it.
Some walk, others run or take the bus, car, bike etc. They leave at different times. They don’t all go the same way or travel at the same speed, so they arrive at the delivery address at different times.
So the pages arrive in a random order and need to be put back into the correct sequence, before the document can be read.
Packets of data work in a similar way. They can be routed in different directions, across different networks at different times. But when they arrive they may need to be put back into their correct sequence so that the information will make sense.
It doesn’t matter that this doesn’t happen in real time the way it would with an analogue signal.
Once the voice signal has been digitized and ‘packetized’ according to the wireless Internet Protocol, it can be transported across networks (a level 3 service) and delivered to the destination address provided they too work with the same set of rules.
Once digitized, the voice message isn’t as vulnerable as it would be during transport with the older real-time analogue systems.
Digital data can be delayed, corrected, filtered and isn’t as easily corrupted by the electrical noise and distortion that can sometimes badly affect analogue signals over conventional voice channels. You may have heard the hiss and strange noises that you would sometimes get with the older analogue phone calls.
As the packets arrive at their destination the data is removed from each and, if part of the service, can be put back into the correct order (a level 4 service). Then the digitized voice signal is converted back to an analogue signal and the original sound is restored… hopefully without any weird noises.
So what products communicate at the Internet level?
IP Products
There are many products designed and manufactured to comply with the Internet Protocol and benefit from being able to communicate and interact with other IP products such as wireless Internet Protocol cameras and Internet Protocol phones.
IPV6 will enable an increasing variety of electronic products to connect directly to each other with a reliable, end-to-end, always-on connection… each with its own dedicated IP address.
Go from Wireless Internet Protocol to How Does Wireless Internet Work